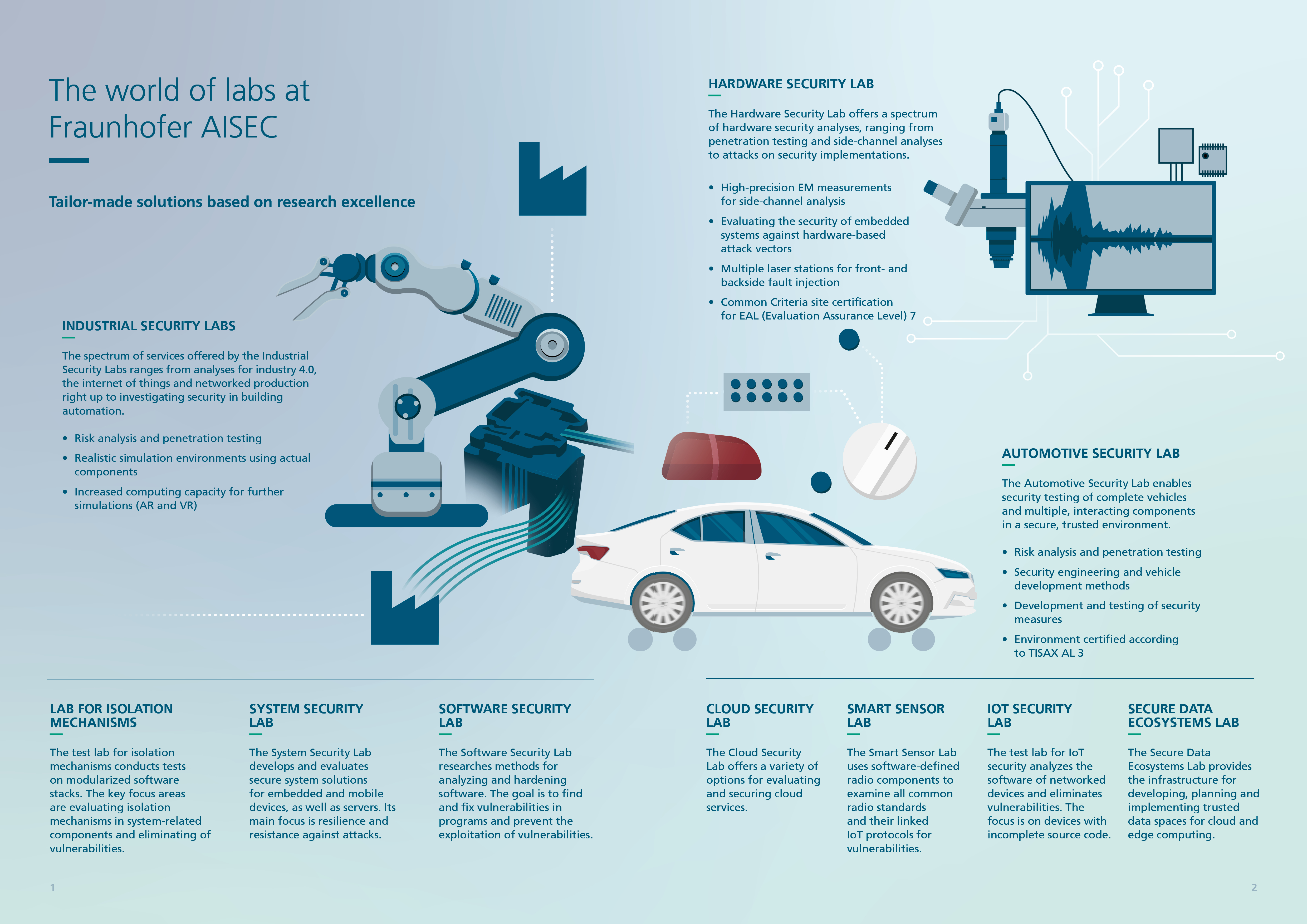
Software Security Lab
In the Software Security Lab, approaches to software analysis and preventive hardening of software are researched. The goal of the researched technologies is on the one hand to find and fix vulnerabilities in programs and on the other hand to prevent the exploitation of vulnerabilities by preventive security measures. To detect vulnerabilities, methods of static code analysis are used (among others), with a focus on system-related programming languages. Memory-unsafe programming languages such as C and C++, as well as memory-safe programming languages such as Rust, are examined. In addition, dynamic software analysis and instrumentation of code are used, such as for efficient fuzzing of software APIs. In software hardening technologies, the focus is on compiler-based security mechanisms, such as control flow integrity (CFI) or memory safety. In addition to the development of new methods, existing approaches from the current state of research are evaluated with respect to their practicability and integrability into existing systems.
Test lab for IoT security
In the test lab for IoT security, the software of networked devices is analyzed with the aim of finding and correcting bugs. The focus is on devices for which the complete source code is usually not available. In the simplest case, external (externally accessible) interfaces (black box) are tested, for example with fuzzing tools. Much more efficient and usually preferable is a setup with access to debug functions of the device to better analyze the behavior. The extraction of the firmware and the static as well as dynamic analysis of the firmware, such as the (partial) execution of the firmware in a simulation environment or a virtual machine as well as the instrumentation of parts of the firmware, is also helpful.
 Fraunhofer Institute for Applied and Integrated Security
Fraunhofer Institute for Applied and Integrated Security