Using the cloud saves users time and money. With modern cloud services, even complex applications can be set up easily and quickly — which is why so many innovative businesses choose this path as a way to remain competitive and successful.
However, the cloud also brings an added layer of complexity: Maintaining control over abstract cloud resources is challenging and complex. Because of this, small and medium-sized businesses in particular often rely on compliance tools to conquer any cloud-related challenges.
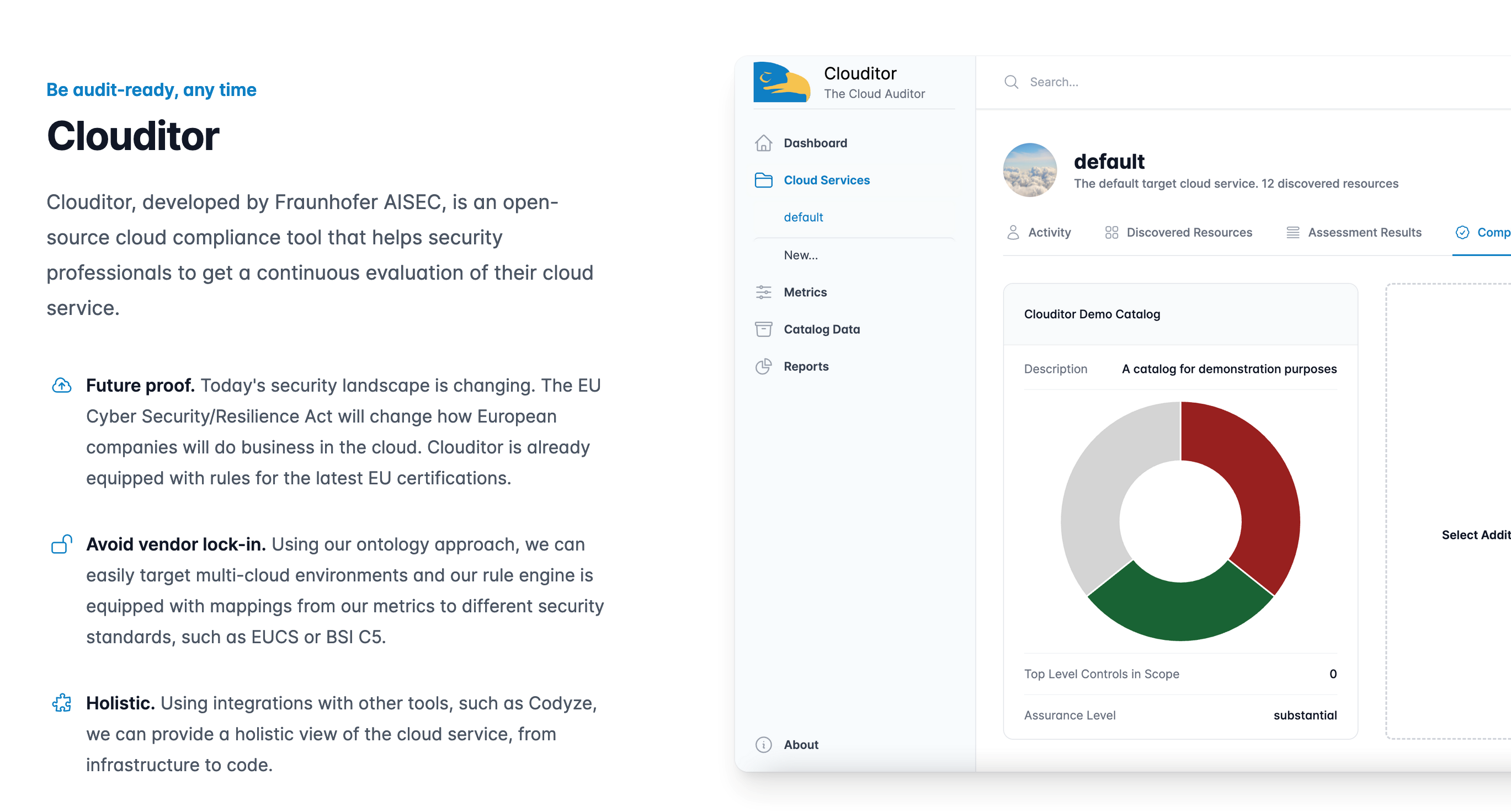
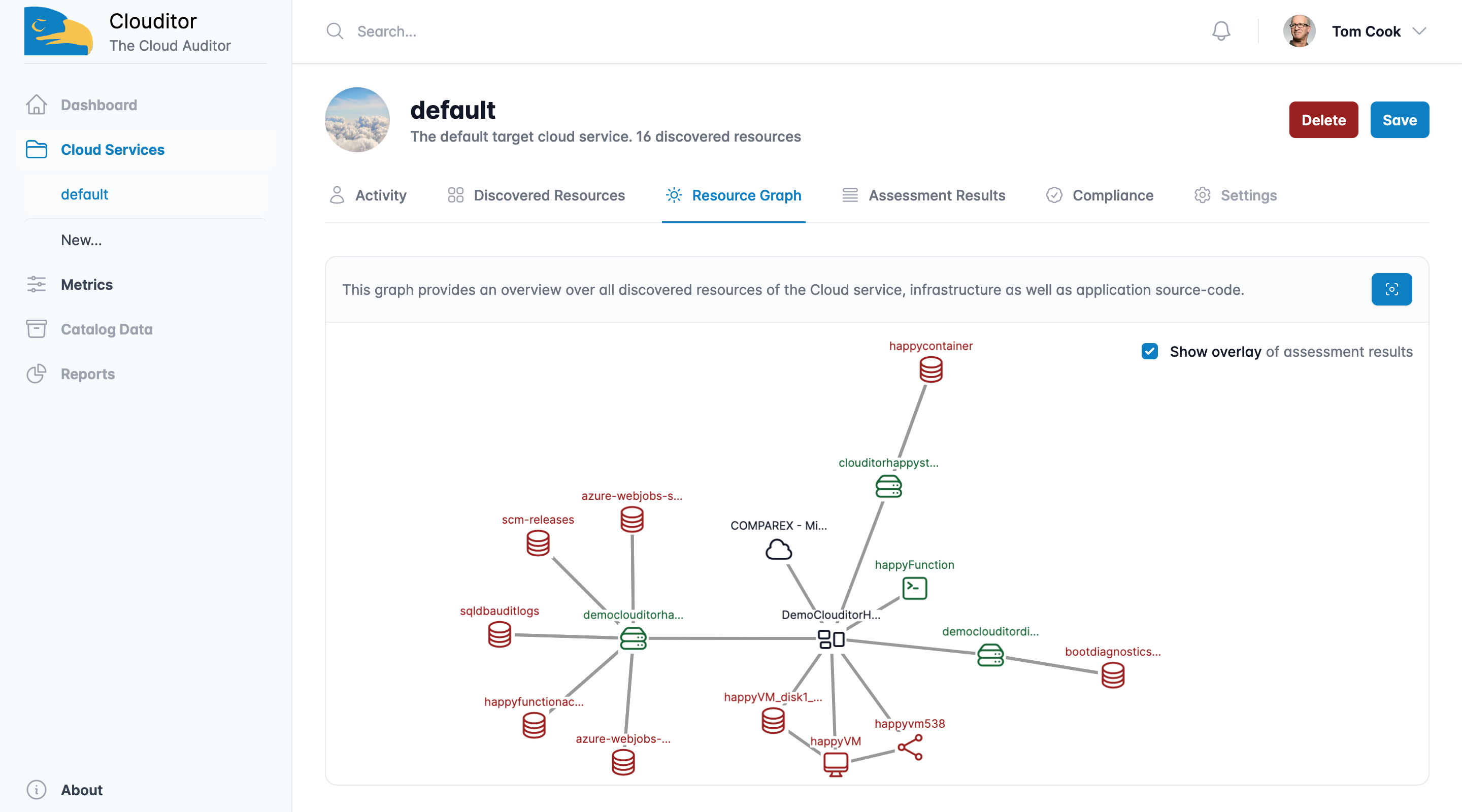
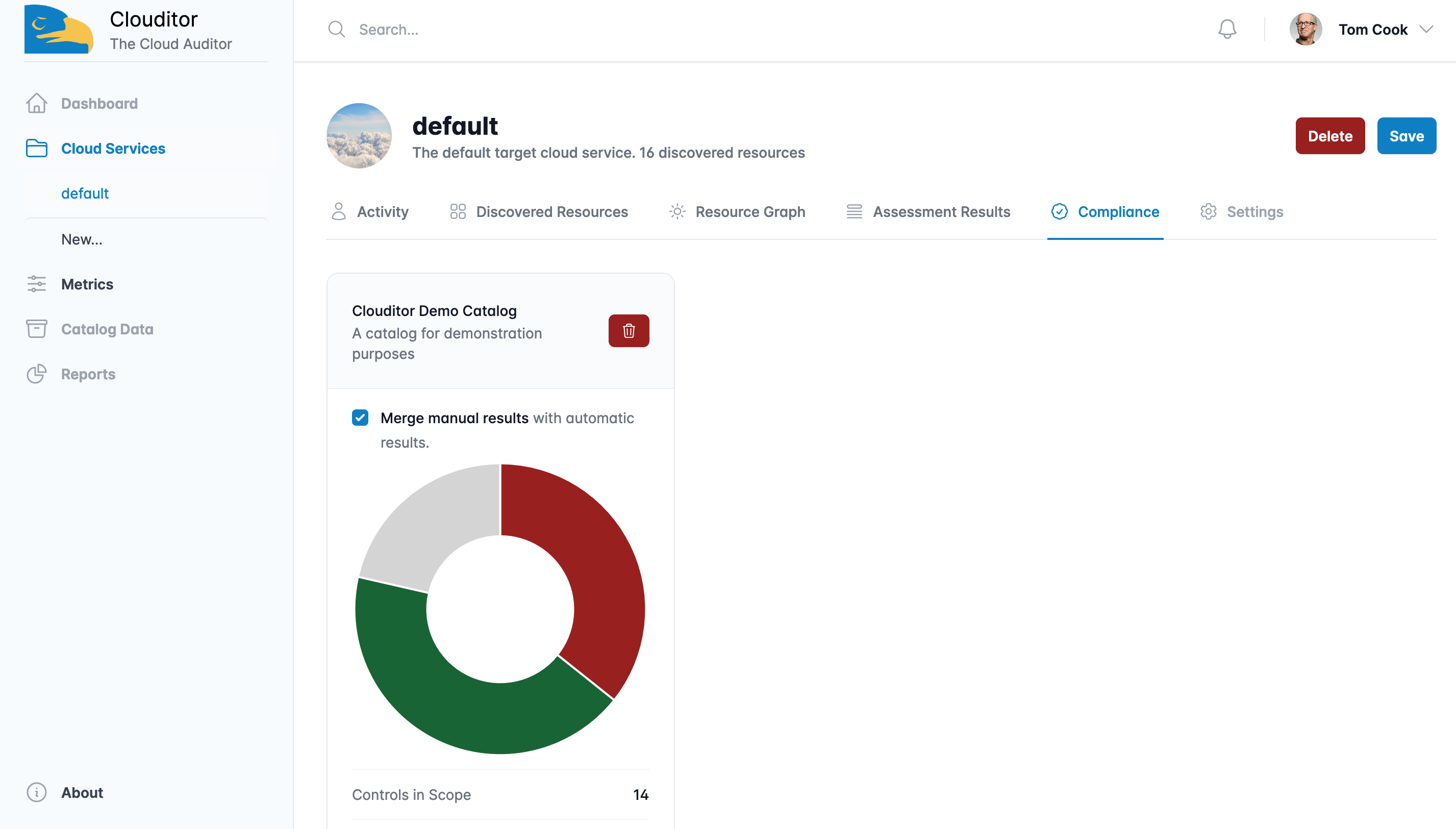
Often, important questions like “Is my application protected against attacks in the cloud?” or “Does a service behave as promised in the SLA?” do not have clear answers. This is where the Clouditor — an assurance tool that automatically poses critical questions to your products and applications and precisely evaluates the results — comes in. It carries out automated tests on your cloud services, before storing and visualizing the results so that they can be processed for a certification audit, for example.
 Fraunhofer Institute for Applied and Integrated Security
Fraunhofer Institute for Applied and Integrated Security